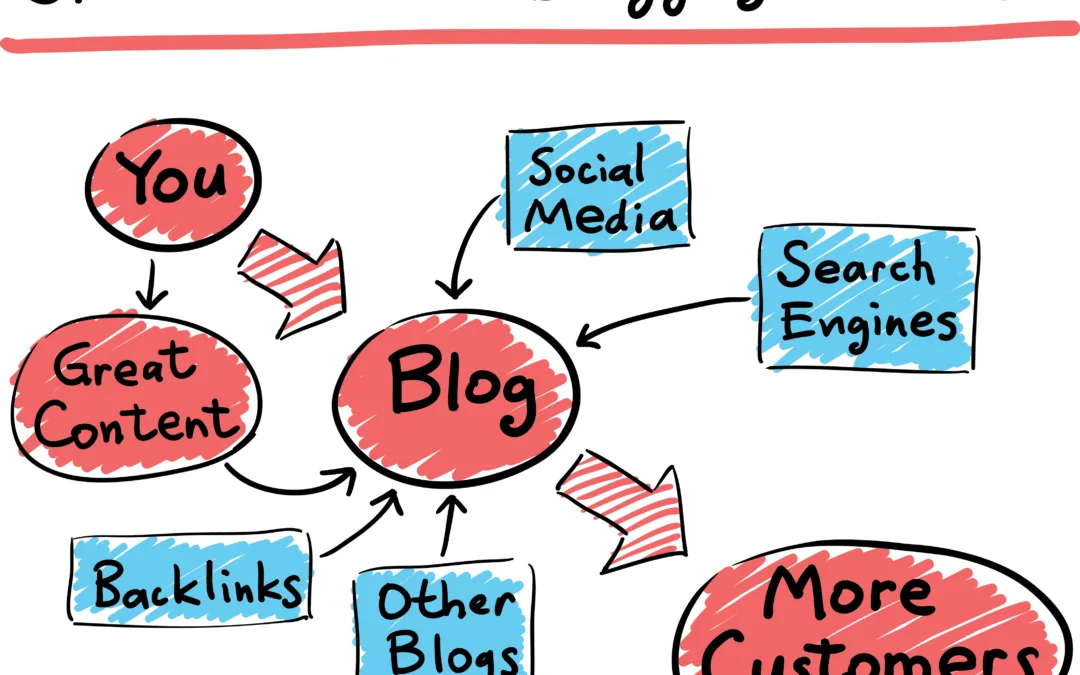
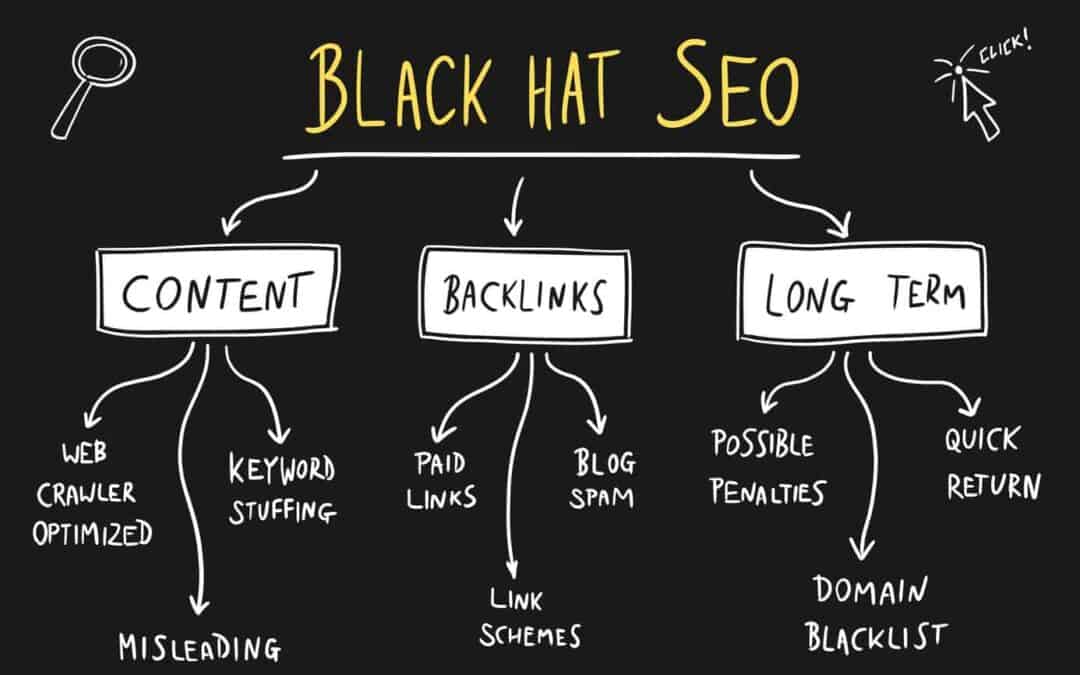
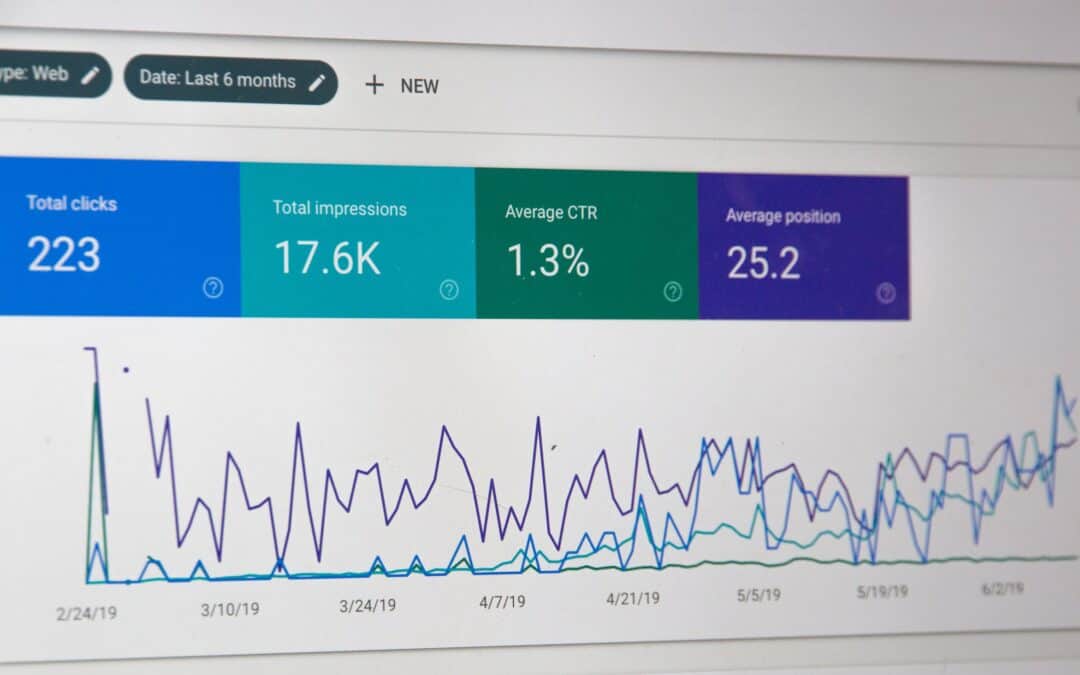
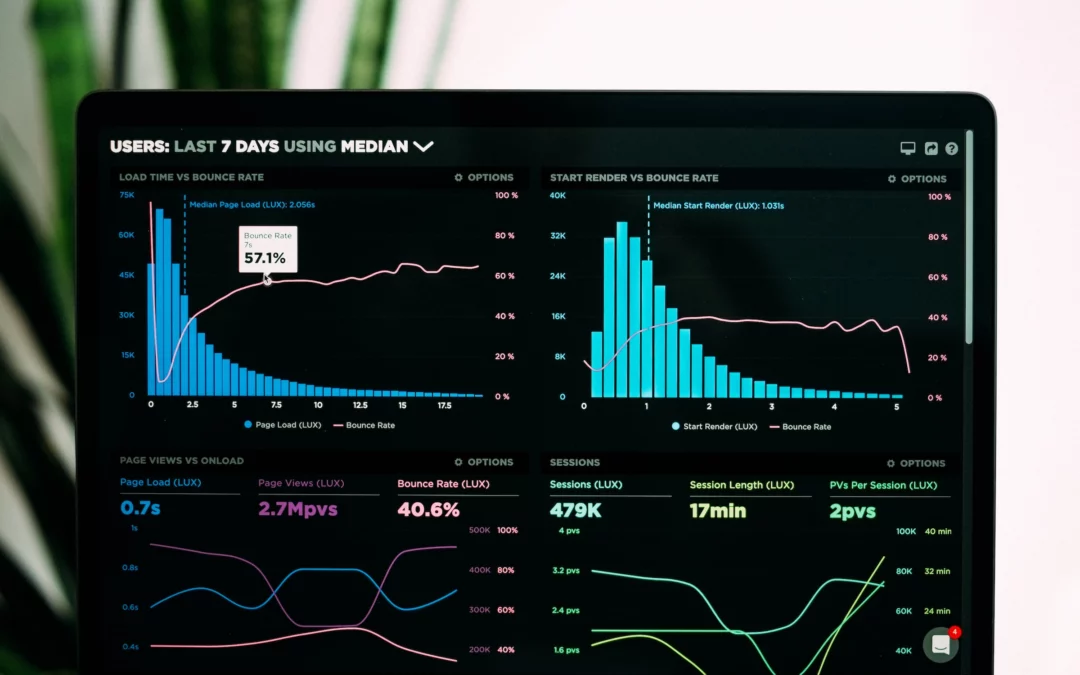
In today’s rapidly evolving digital landscape, digital marketing in Fort Collins has shifted from a “nice-to-have” to an absolute necessity for businesses of all sizes. Are you struggling to reach your ideal customers online? Wondering how to leverage data-driven...