Unlocking the Power of Visual Advertising: Understanding the Difference between Display Ads and...

iPoint Insights (blog)

Unlocking the Power of Visual Advertising: Understanding the Difference between Display Ads and...

In the ever-evolving digital landscape, the importance of accessibility cannot be overstated. As...

In the fast-paced and ever-evolving landscape of technology, small businesses often find...
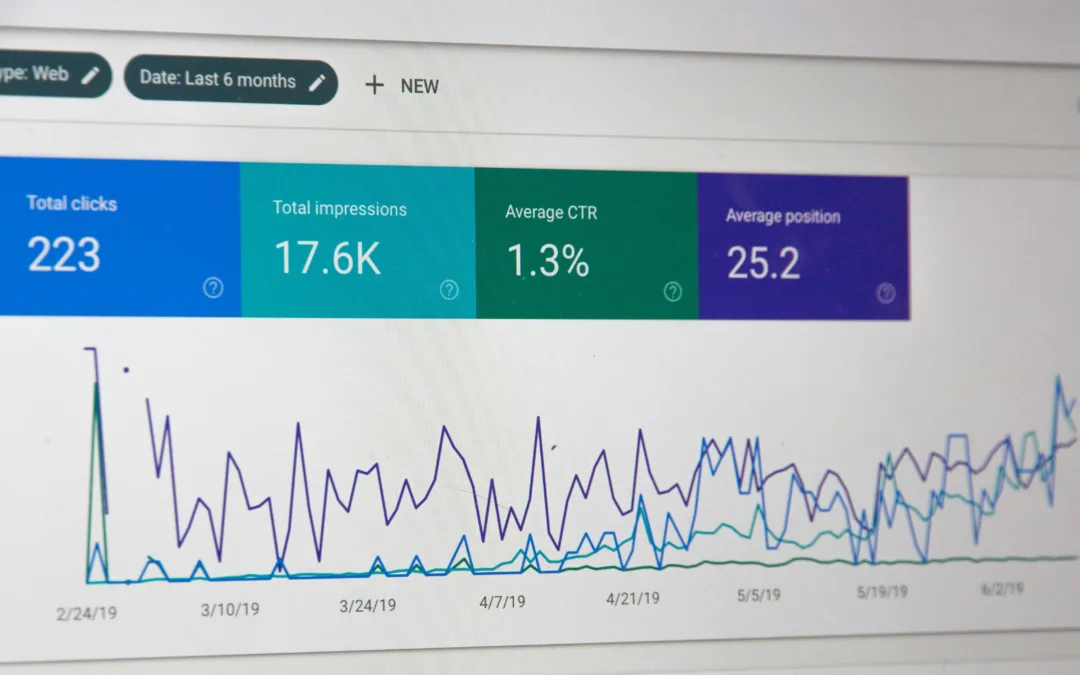
In the ever-evolving landscape of digital marketing, the game-changer is the ability to harness...

In the ever-evolving landscape of B2B marketing, email continues to be a powerful tool for...

The decision to redesign your business website is a significant step toward enhancing your online...
We’ve all seen them. From that dashing Nigerian Prince who promises you riches to that text with a mystery parcel who needs your “delivery preferences”, phishing scams are more convincing than ever these days. Next time you come across an email that seems…well, phishy, take some time to think. Educating yourself on what makes up a phishing scam will help you better protect yourself and your loved ones.
According to phishing.org, “Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords”.
Phishing scams have gotten more advanced over the years and are becoming more difficult to spot, due to the fact that they use names and information personalized to you. They also usually are too good to be true (Not today, my sweet Nigerian Prince), or, have a sense of urgency. People can get flustered by the sense of urgency, making them less likely to pay attention to details.
For example, I have received emails at my office that look like they are coming from my boss, Pete Fardal. It’s addressed with his name, and the email requests that I help him with a task, then asks for my personal phone number. Creepy, right?
After investigating further, I noticed that I didn’t recognize the email address. Pete confirmed that he sent no such email, but it was very convincing. Heck, the senders even knew that Pete was one of my supervisors! Our office has even received mail-in scams, where they are physical letters asking for personal information.
Phishing scams start with an attacker who wants you to take some sort of action so that they can reach their goal – to compromise control of your computer, or to steal private information (identity, passwords, & financial access).
It’s called “phishing” because the attacker is dangling bait in front of you (promise of money, gifts, a high stake situation, etc), hoping that you’ll bite. Once you bite, you’ll realize that it was just a sad, fake worm and you’re stuck with a hook though your face. Ouch.
I’ll use a currently rampant phishing scam to help explain how they work. In 2020, many people have received a text message posed to be from a mailing service, alerting you that you need to enter delivery details for a package that’s waiting for you. Once you click the link, you are taken to a fake amazon page and promised a free (expensive) prize for completing a survey.
At the end of the survey, you’re invited to enter credit card information – since you *only* have to pay for shipping and handling. Little do you know, written in the fine print is permission to make you a subscriber to their service, allowing them to charge you a monthly fee and steal your money.

These phishing scams are an extra threat to internet safety because they are more convincing than some other forms of scamming. You can block one sender, and it’ll come back to you from a different number. So, how do you best protect your personal information? Ask yourself these questions next time you’re unsure if a message is phony or not:
Phishing scams aren’t going away anytime soon, so make sure that you’re aware of their tactics. Asking yourself these questions may save you a lot of regret (and money) in the future. If you’re looking to strengthen your network security, check out our networking services or contact us for a complimentary consultation. Now, get out there and practice some good internet safety!