Unlocking the Power of Visual Advertising: Understanding the Difference between Display Ads and...

iPoint Insights (blog)

Unlocking the Power of Visual Advertising: Understanding the Difference between Display Ads and...

In the ever-evolving digital landscape, the importance of accessibility cannot be overstated. As...

In the fast-paced and ever-evolving landscape of technology, small businesses often find...
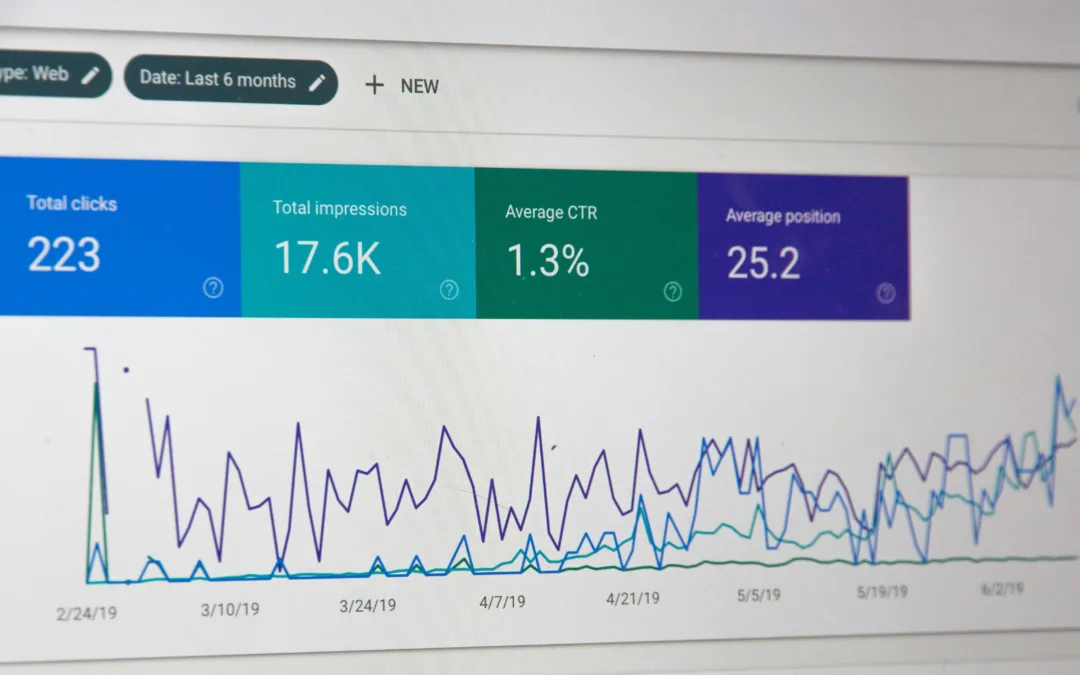
In the ever-evolving landscape of digital marketing, the game-changer is the ability to harness...

In the ever-evolving landscape of B2B marketing, email continues to be a powerful tool for...

The decision to redesign your business website is a significant step toward enhancing your online...
In an increasingly interconnected world, the protection of digital assets has become a paramount concern. As technology advances, so do the tactics of cybercriminals seeking to exploit vulnerabilities. In this landscape, the principle of layered security emerges as a powerful defense strategy. Whether applied to information technology (IT) or website maintenance, layered security offers a multifaceted approach that fortifies digital domains against a diverse range of threats. In this blog post, we will explore the concept of layered security and how it applies to both IT and the maintenance of websites.
Layered security, often referred to as defense in depth, is a comprehensive approach to security that involves the deployment of multiple layers of protection, each acting as a barrier to potential threats. The concept draws inspiration from real-world fortifications, such as castles with moats, drawbridges, walls, and towers—each layer adding an additional obstacle for attackers.
In the realm of information technology, the principle of layered security manifests as a collection of security measures that collectively create a robust defense against cyber threats:
Just as in IT, applying the layered security principle to website maintenance bolsters protection against digital threats and vulnerabilities:
Conclusion
In a world where digital threats constantly evolve, relying on a singular security measure is no longer sufficient. Embracing the layered security principle provides a comprehensive and effective approach to safeguarding both information technology and websites. By erecting multiple barriers against potential threats, organizations and individuals can fortify their digital realms and confidently navigate the dynamic landscape of the digital age. Remember, just as layers of armor protect a knight in battle, layers of security shield your digital assets from the onslaught of cyber adversaries.