Unlocking the Power of Visual Advertising: Understanding the Difference between Display Ads and...

iPoint Insights (blog)

Unlocking the Power of Visual Advertising: Understanding the Difference between Display Ads and...

In the ever-evolving digital landscape, the importance of accessibility cannot be overstated. As...

In the fast-paced and ever-evolving landscape of technology, small businesses often find...
In the ever-evolving landscape of digital marketing, the game-changer is the ability to harness...

In the ever-evolving landscape of B2B marketing, email continues to be a powerful tool for...

The decision to redesign your business website is a significant step toward enhancing your online...
Email attachments can be incredibly useful for sharing files and documents quickly and easily. However, they can also be a major source of security risks. Suspicious email attachments can infect your computer with malware, ransomware, or viruses, or they can be used to steal sensitive information. In this blog post, we’ll explore which email attachments are safe, which ones are not safe, and how to determine this.
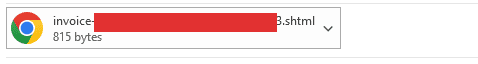
How to Determine the File Type of an Email Attachment: When an email has an attachment, you will likely see an icon in the email preview that looks like a paperclip. If/when you open the email, the attachment will show in the head of the email, just underneath the sender and recipient information. The file name will appear at the end of the title of the file. The example below is an SHTML file:
Safe email attachments are files that are not infected with malware, viruses, or other harmful software. They can include a variety of file types, such as documents, spreadsheets, images, and PDFs. Here are some examples of safe email attachments:
1. Word Documents and Spreadsheets
Word documents and spreadsheets are commonly used for business purposes and are generally safe to send and receive via email. However, it is important to scan these files for viruses before opening them, especially if they are coming from an unknown source.
2. Images
Images, such as JPG, PNG, and GIF files, are also generally safe to send and receive via email. They are commonly used for sharing pictures and graphics and are not typically associated with security risks.
3. PDFs
PDFs are a popular file format for sharing documents and are generally safe to send and receive via email. However, like with other file types, it is important to scan these files for viruses before opening them.
Unsafe Email Attachments
Unsafe email attachments are files that contain viruses, malware, or other harmful software. These attachments can be disguised as harmless files, such as a PDF or Word document, and can infect your computer if you open them. Here are some examples of unsafe email attachments:
Executable files, such as .exe or .bat files, are a major source of security risks and should never be sent or received via email. These files are designed to run programs on your computer and can be used to install malware or other harmful software.
ZIP files are compressed files that can contain multiple files and folders. While they can be useful for sharing large amounts of data, they can also be used to hide malicious files. It is important to scan ZIP files for viruses before opening them, and it is best to avoid opening them altogether if they come from an unknown source.
3. HTML and SHTML FilesHTML and SHTML file attachments in emails are always suspicious, and usually a phishing attack. These files often simulate website login pages, such as your email login, and are designed to look indistinguishable to a genuine login page so the recipient enters their log in information, and then the attacker has it.
4. ScriptsScripts, such as .js or .vbs files, are also a major source of security risks and should never be sent or received via email. These files can be used to execute malicious code on your computer and can be used to install malware or other harmful software.
Determining if an email attachment is safe can be challenging, especially if you are not familiar with the sender. Here are some tips for determining if an email attachment is safe:
One of the best ways to determine if an email attachment is safe is to check the sender. If the email is from a trusted source, such as a coworker or friend, it is likely safe to open. However, if the email is from an unknown sender or a suspicious-looking email address, it is best to err on the side of caution and avoid opening any attachments.
Another way to determine if an email attachment is safe is to scan it for viruses. Many antivirus programs have an email scanning feature that can scan attachments before they are opened. If your antivirus program detects a virus, it will typically quarantine the file and notify you of the threat.
Finally, it is important to use common sense when opening email attachments. If an attachment seems suspicious or too good to be true, it probably is. Avoid opening attachments that claim to offer free products or services, as these are often used