Unlocking the Power of Visual Advertising: Understanding the Difference between Display Ads and...

iPoint Insights (blog)

Unlocking the Power of Visual Advertising: Understanding the Difference between Display Ads and...

In the ever-evolving digital landscape, the importance of accessibility cannot be overstated. As...

In the fast-paced and ever-evolving landscape of technology, small businesses often find...
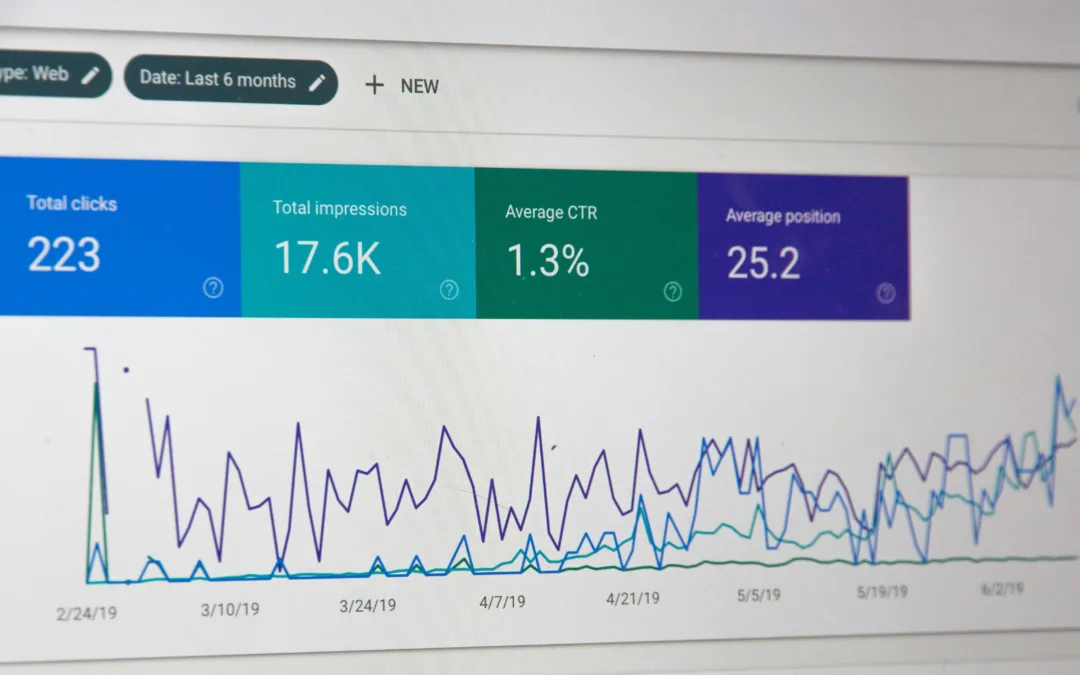
In the ever-evolving landscape of digital marketing, the game-changer is the ability to harness...

In the ever-evolving landscape of B2B marketing, email continues to be a powerful tool for...

The decision to redesign your business website is a significant step toward enhancing your online...
Every year, we hear more and more about cyber-attacks, and it is forecasted to only get worse: Cybercrime Magazine predicts that businesses will lose about $10.5 trillion in 2025. In today’s post, we hope to clarify some of the principles of Information Security (also known as infosec) so you can be a little more prepared. The 3 Principles of Information Security are the foundation for every preventative effort in the world of information security, including our risk-assessment program.
Confidentiality
Confidentiality is the first principle of information security. Confidentiality is defined as measures designed to prevent the unauthorized broadcasting or disclosure of information. Simply put, confidentiality is any effort to keep private information private. This is incredibly important for any organization, but it becomes paramount for any company that handles and processes credit card information, insurance information, HIPAA information, and any personally identifying information.
Confidentiality is so important that most industries have created their own security standards to comply with to ensure the privacy of clients and customers. For example, any company that processes payment information is required to be PCI (Payment Card Industry) compliant. Confidentiality is fundamental to any information security procedure.
Integrity
In the world of information security, integrity is the second leading principle. Integrity ensures that the confidential information is accurate and unaltered. In other words, integrity means that whoever you partner with to handle your secure information promises to not change or delete files that you entrust to them, and that they promise to protect data from being altered. Integrity is what allows businesses to trust security professionals with their private information.
Availability
The third and final principal of information security is availability. In context, availability is the ease through which authorized individuals can access the protected data as needed. After all, if the designated people cannot reach the private information they need, it defeats the purpose of having it. Cloud storage, such as that used in iPoint’s Remote Backup program, is an excellent example of this.
While it is good to know the principles that act as a foundation for Information Security, many business owners struggle with how to apply them to their business, which is perfectly understandable! Information Security is a complicated topic, with a growing industry that has a demand that increases every single year.
If you feel as though your team may not be prepared to handle the prevention of a data incident, we want to reassure you that we have plenty of services that simplify this process for you, which can be purchased either in packages, or ala-carte. Namely, we would like to recommend checking out a few different services we offer.
iPoint’s Risk Assessment service is an in-depth analysis of your network, which is then used to identify vulnerable areas. Of course, if a vulnerability is found, recommendations will be made. You can read more about Risk Assessment by clicking here.
In addition, iPoint’s Network Monitoring service is a great option for anyone looking to protect their information! Network monitoring watches your network for breaches, viruses, and many other technical issues that can impact your business.
We hope this was helpful! If you have any questions or would like to start discussing network management for your company, give us a call at (970) 266-0703.